Project Octopus - Think dropbox for VMware yet enables Hybrid dropbox clouds too
Project Appblast - Like Citrix Access Gateway or Xen App but not Citrix Receiver as it is all HTML5!
Project Octopus - Think dropbox for VMware yet enables Hybrid dropbox clouds too
Project Appblast - Like Citrix Access Gateway or Xen App but not Citrix Receiver as it is all HTML5!

Vyatta to Cisco - Tunneling from ASA to Vyatta Using VMware and GNS from Roggy on Vimeo.


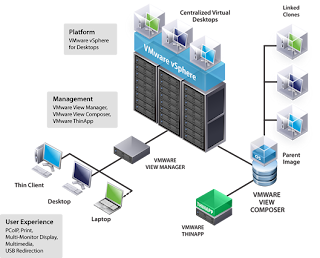
VMware View 4 - Part 1 from Roggy on Vimeo.
VMware View 4 - Part 2 from Roggy on Vimeo.



devices.hotplug = "false"


Managed Service Provider using Vyatta (OpenVPN) and PRTG to monitor Customers - Part 1 from Richard Vimeo on Vimeo.
Managed Service Provider using Vyatta (OpenVPN) and PRTG to monitor Customers - Part 2 from Richard Vimeo on Vimeo.
Network Monitoring/Sniffing using vSphere and PRTG Ver 2 - Part 1 from Richard Vimeo on Vimeo.
Network Monitoring/Sniffing using vSphere and PRTG Ver 2 - Part 2 from Richard Vimeo on Vimeo.

Windows 2003 Clustering with EMC Celerra VM -Intro from Richard Vimeo on Vimeo.
Some Commands you might find handy:
Change hostname /etc/host - new ip address hostname
/etc/sysconfig/network - domainname=cookie.local
hostname=cel1
service network restart
export NAS_DB=/nas
(root - ssl trust)
/nas/sbin/rootnas_cel -list
/nas/sbin/rootnas_cel -update id=0
/nas/sbin/nas_config -ssl
/nas/sbin/js_fresh_restart
nas_license -init
/opt/blackbird/tools init_storageID
Windows 2003 Clustering with EMC Celerra VM -Part1 from Richard Vimeo on Vimeo.
Windows 2003 Clustering with EMC Celerra VM -Part2 from Richard Vimeo on Vimeo.
Windows 2003 Clustering with EMC Celerra VM -Part3 from Richard Vimeo on Vimeo.
Network Monitoring/Sniffing using vSphere and PRTG - Part 1 from Richard Vimeo on Vimeo.
Network Monitoring/Sniffing using vSphere and PRTG - Part 2 from Richard Vimeo on Vimeo.

system-config-network
edit /etc/hosts
service network restart
yum groupinstall "Clustering"
yum groupinstall "Cluster Storage"
yum groupinstall "Windows File Server"
chkconfig --del smb
yum install iscsi-initiator-utils
service iscsi start
iscsiadm -m discovery -t sendtargets -p 192.168.1.3
service iscsi restart
fdisk -l
mkqdisk -c /dev/sdb -l quorum
luci_admin init
Samba Cluster with GFS 2, Centos 5, iSCSI and Openfiler - Part 1 from Richard Vimeo on Vimeo.
mkfs.gfs2 -p lock_dlm -t cluster1:sanvol1 -j 4 /dev/sdc
mkdir /san
mkdir /san/sanvol1
service ricci restart
service qdiskd restart
chkconfig luci on
chkconfig qdiskd on
(do node2)
use luci to create cluster
Quorum parameters:
interval=1
votes=1
tko=10
min score=1
heuristics=ping -c2 -t1 192.168.1.3
mount /dev/sdc /san/sanvol1
gfs2_tool list
gfs2_tool df
umount /san/sanvol1
cman_tool status
Samba Cluster with GFS 2, Centos 5, iSCSI and Openfiler - Part 2 from Richard Vimeo on Vimeo.
Configure Resources:
IP
GFS
Samba
Configure failover Domains
Configure Shared Fencing Device (then nodes)
Add Services
workgroup = cookie
server string = Samba Server Version %v
bind interfaces only = yes
interfaces = 10.0.1.100
netbios name = cluster1
local master = no
domain master = no
preferred master = no
password server = None
guest ok = yes
guest account = root
security = SHARE
dns proxy = no
[sanvol]
comment = High Availability Samba Service
browsable = yes
writable = yes
public = yes
path = /san/sanvol1
guest ok=yes
create mask=0777
smbpasswd -a root
scp /etc/samba/smb.conf.cluster1 node2:/etc/samba/
restart smb
redo services - ip-GFS-samba
soft reboot
Samba Cluster with GFS 2, Centos 5, iSCSI and Openfiler - Part 3 from Richard Vimeo on Vimeo.
Samba Cluster with GFS 2, Centos 5, iSCSI and Openfiler - Part 4 from Richard Vimeo on Vimeo.

Wired 802.1x Port Authentication with Certificate Auto Enrolment Part1 from Richard Vimeo on Vimeo.
Wired 802.1x Port Authentication with Certificate Auto Enrolment Part2 from Richard Vimeo on Vimeo.
Wired 802.1x Port Authentication with Certificate Auto Enrolment Part3 from Richard Vimeo on Vimeo.