Hi again,
This post starts like a song "..I was working in the lab late one night" and I was playing around with cisco queueing and traffic shaping and whilst working on something for a client I worked out something that maybe be obvious for most but I have never really seen it in any forums/cisco documentation.
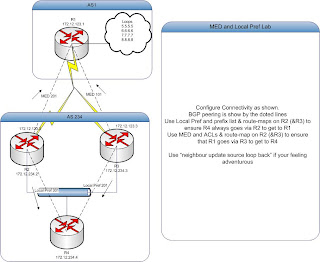
Anyway here is the visio of the scenario:

Here is how I did it.
1) Define the ACLs (These are used later for the Class-maps)-Pings
access-list 110 permit icmp 10.10.0.0 0.0.0.255 any
-Voip
access-list 120 permit ip 10.10.0.0 0.0.0.255 host 192.168.0.5
-DNS
access-list 130 permit tcp 10.10.0.0 0.0.0.255 any eq domain
-Http
access-list 140 permit tcp 10.10.0.0 0.0.0.255 any eq www
-Bulk traffic
access-list 160 permit ip host 192.168.0.3 any
2) Define the class-maps:class-map match-all VOIP
match access-group 110
match access-group 120
class-map match-all PING
match access-group 110
class-map match-all HTTP
match access-group 140
class-map match-all DNS
match access-group 130
3)
Create 2 policy maps. This is because you can only really control outgoing bandwidth therefore you control WAN upstream on the WAN interface
But you control WAN downstream on the LAN interface.*****************************************
policy-map WAN_OUT
class PING
bandwidth 1024
class VOIP
priority 1024
class DNS
bandwidth 1024
class HTTP
bandwidth 4096
class class-default
fair-queue
*****************************************
policy-map LAN_OUT
class PING
bandwidth 1024
class VOIP
priority 1024
class DNS
bandwidth 1024
class HTTP
bandwidth 4096
class class-default
fair-queue
*****************************************
Then I decided to cap all downstream traffic from 192.168.0.3 to about 256KB/s
This command make sure that when a user downloads a file it can never exceed this amount
(even when not congested)
interface FastEthernet0/1
..
rate-limit output access-group 160 2000000 1000000 1000000 conform-action continue exceed-action drop
..
Notice once again at this command is applied to the LAN interface on the output.
Once finished I used http://www.testyourvoip.com to test the quality whilst user 10.10.0.3 was downloading from the internet, grabing files over FTP & SMB from 192.168.0.3.
...and it worked! scored about 4.5 where as before shaping I had a score of about 3-ish
This isnt perfect, but it was just designed to show that you dont use the input queue on the wan interface to control your downloading you use the output queue on your lan interface.Hope this helps some people out there.