Which is a nice TLA for Multipoint GRE(Tunnel), NHRP(Next Hop Routing Protocol) and IPSEC.
So here is the lab:
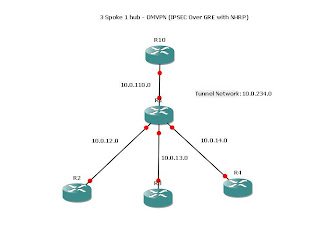
Very boring compared to the MPLS L2 lab however there are some important techs to get used to.
For the purposes of the lab, R1 is not under our control.
Therefore all the spoke routers have a default route to the R1 and that is it.
It is up to the DMVPN to fill in the gaps.
Here is R10 which is the HQ or "Hub" router.
interface Tunnel0
!All the tunnels have to be in the same subnet
ip address 10.0.234.10 255.255.255.0
no ip redirects
ip mtu 1400
!Dynamically map to the spokes
ip nhrp map multicast dynamic
!Network-id has to be the same on all routers
ip nhrp network-id 1
ip nhrp holdtime 450
ip tcp adjust-mss 1360
!This is needed as OSPF auto-configs a "tunnel int" as point-to-point which is wrong !here
ip ospf network point-to-multipoint
!Exit interface
tunnel source FastEthernet1/0
!Tunnel mode
tunnel mode gre multipoint
R2
interface Tunnel0
ip address 10.0.234.2 255.255.255.0
no ip redirects
ip mtu 1400
ip nhrp map multicast 10.0.110.10
ip nhrp map 10.0.234.10 10.0.110.10
ip nhrp network-id 1
ip nhrp holdtime 450
ip nhrp nhs 10.0.234.10
ip tcp adjust-mss 1360
ip ospf network point-to-multipoint
tunnel source FastEthernet1/0
tunnel mode gre multipoint
R3
!
interface Tunnel0
ip address 10.0.234.3 255.255.255.0
no ip redirects
ip mtu 1400
ip nhrp map multicast 10.0.110.10
ip nhrp map 10.0.234.10 10.0.110.10
ip nhrp network-id 1
ip nhrp holdtime 450
ip nhrp nhs 10.0.234.10
ip tcp adjust-mss 1360
ip ospf network point-to-multipoint
tunnel source FastEthernet1/0
tunnel mode gre multipoint
R4
interface Tunnel0
ip address 10.0.234.4 255.255.255.0
no ip redirects
ip mtu 1400
ip nhrp map multicast 10.0.234.10
ip nhrp map 10.0.234.10 10.0.110.10
ip nhrp network-id 1
ip nhrp holdtime 450
ip nhrp nhs 10.0.234.10
ip tcp adjust-mss 1360
ip ospf network point-to-multipoint
tunnel source FastEthernet1/0
tunnel mode gre multipoint
That should be the tunnel up. At this point you can test the tunnel by ping the Hub tunnel address 10.0.234.10 from each of the spokes.
Now encryption:
R10
crypto isakmp policy 100
encr aes
authentication pre-share
group 2
crypto isakmp key letmein address 0.0.0.0 0.0.0.0
!
!
crypto ipsec transform-set TUN-TRANSFORM esp-aes esp-sha-hmac
!
crypto ipsec profile TUN-PROFILE
set transform-set TUN-TRANSFORM
Then applied to the Tunnel inteface:
interface Tunnel0
ip address 10.0.234.10 255.255.255.0
no ip redirects
ip mtu 1400
ip nhrp map multicast dynamic
ip nhrp network-id 1
ip nhrp holdtime 450
ip tcp adjust-mss 1360
ip ospf network point-to-multipoint
tunnel source FastEthernet1/0
tunnel mode gre multipoint
tunnel protection ipsec profile TUN-PROFILE
!
then the same for R2,R3,R4:
crypto isakmp policy 100
encr aes
authentication pre-share
group 2
crypto isakmp key letmein address 0.0.0.0 0.0.0.0
!
!
crypto ipsec transform-set TUN-TRANSFORM esp-aes esp-sha-hmac
!
crypto ipsec profile TUN-PROFILE
set transform-set TUN-TRANSFORM
!
~Under the Tunnel0 interface:
!
tunnel protection ipsec profile TUN-PROFILE
!
This is identicial for each spoke.
Then an example OSPF config on R2:
!
router ospf 1
router-id 2.2.2.2
log-adjacency-changes
network 2.2.2.2 0.0.0.0 area 0
network 10.0.234.0 0.0.0.255 area 0
network 192.168.2.0 0.0.0.255 area 2
!
Done!
