So that lab today is for connecting a Vyatta router to a Cisco ASA/PIX and creating a Lan to Lan Tunnel with some one to one src/dst NAT thrown in for good measure :)
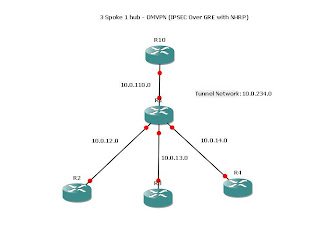
Here is the lab:

Here is the proof that is works:
Vyatta to Cisco - Tunneling from ASA to Vyatta Using VMware and GNS from Roggy on Vimeo.
Vyatta config:
interfaces {
ethernet eth0 {
address 10.0.19.1/24
address 10.0.19.10/24
duplex auto
hw-id 00:0c:29:5d:91:c6
smp_affinity auto
speed auto
}
ethernet eth1 {
address 192.168.10.1/24
duplex auto
hw-id 00:0c:29:5d:91:d0
smp_affinity auto
speed auto
}
ethernet eth2 {
duplex auto
hw-id 00:0c:29:5d:91:da
smp_affinity auto
speed auto
}
loopback lo {
}
}
protocols {
static {
route 0.0.0.0/0 {
next-hop 10.0.19.9 {
}
}
}
}
service {
nat {
rule 5 {
destination {
address 10.20.0.0/24
}
exclude
outbound-interface eth0
source {
address 192.168.10.0/24
}
type masquerade
}
rule 100 {
outbound-interface eth0
outside-address {
address 10.0.19.10
}
source {
address 192.168.10.10
}
type source
}
rule 110 {
destination {
address 10.0.19.10
}
inbound-interface eth0
inside-address {
address 192.168.10.10
}
protocol tcp
type destination
}
rule 900 {
outbound-interface eth0
source {
address 192.168.10.0/24
}
type masquerade
}
}
ssh {
allow-root
port 22
protocol-version v2
}
}
system {
host-name R1
login {
user vyatta {
authentication {
encrypted-password $1$Oxg1L7oM$v4Vi.4pW3Ai/fPFIzpDzC0
}
level admin
}
}
ntp-server 0.vyatta.pool.ntp.org
package {
auto-sync 1
repository community {
components main
distribution stable
password ""
url http://packages.vyatta.com/vyatta
username ""
}
}
syslog {
global {
facility all {
level notice
}
facility protocols {
level debug
}
}
}
time-zone GMT
}
vpn {
ipsec {
esp-group ESP-1W {
compression disable
lifetime 3600
mode tunnel
pfs disable
proposal 1 {
encryption 3des
hash sha1
}
}
ike-group IKE-1W {
lifetime 86400
proposal 1 {
dh-group 2
encryption 3des
hash sha1
}
}
ipsec-interfaces {
interface eth0
}
nat-traversal enable
site-to-site {
peer 10.0.29.2 {
authentication {
mode pre-shared-secret
pre-shared-secret letmein
}
ike-group IKE-1W
local-ip 10.0.19.1
tunnel 1 {
allow-nat-networks disable
allow-public-networks disable
esp-group ESP-1W
local-subnet 192.168.10.0/24
remote-subnet 10.20.0.0/24
}
}
}
}
}
/* Warning: Do not remove the following line. */
/* === vyatta-config-version: "webgui@1:dhcp-server@4:conntrack-sync@1:firewall@3:qos@1:webproxy@1:vrrp@1:nat@3:ipsec@2:wanloadbalance@2:cluster@1:system@3:quagga@2:dhcp-relay@1" === */
Pix Config:
!
PIX Version 8.0(2)
!
hostname FW1
enable password 8Ry2YjIyt7RRXU24 encrypted
names
!
interface Ethernet0
nameif outside
security-level 0
ip address 10.0.29.2 255.255.255.0
!
interface Ethernet1
nameif inside
security-level 100
ip address 10.20.0.1 255.255.255.0
!
interface Ethernet2
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet3
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet4
shutdown
no nameif
no security-level
no ip address
!
passwd 2KFQnbNIdI.2KYOU encrypted
ftp mode passive
access-list icmp extended permit icmp any any
access-list NO-NAT extended permit ip 10.20.0.0 255.255.255.0 192.168.10.0 255.255.255.0
access-list IPSEC-TUN extended permit ip 10.20.0.0 255.255.255.0 192.168.10.0 255.255.255.0
pager lines 24
mtu outside 1500
mtu inside 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
global (outside) 1 interface
nat (inside) 0 access-list NO-NAT
nat (inside) 1 0.0.0.0 0.0.0.0
access-group icmp in interface outside
access-group icmp out interface outside
access-group icmp in interface inside
access-group icmp out interface inside
route outside 0.0.0.0 0.0.0.0 10.0.29.9 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout uauth 0:05:00 absolute
dynamic-access-policy-record DfltAccessPolicy
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
crypto ipsec transform-set FW1-TRANSFORM esp-3des esp-sha-hmac
crypto map FW1 10 match address IPSEC-TUN
crypto map FW1 10 set peer 10.0.19.1
crypto map FW1 10 set transform-set FW1-TRANSFORM
crypto map FW1 interface outside
crypto isakmp identity address
crypto isakmp enable outside
crypto isakmp policy 100
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
no crypto isakmp nat-traversal
telnet timeout 5
ssh timeout 5
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
!
!
tunnel-group 10.0.19.1 type ipsec-l2l
tunnel-group 10.0.19.1 ipsec-attributes
pre-shared-key letmein
prompt hostname context
Enjoy!