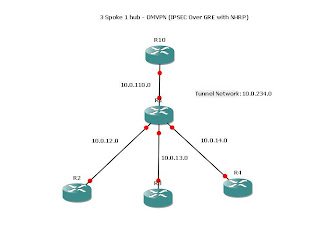
This is the practical to this lab: here
First the boring stuff, setting up IP connectivity:
R1
interface FastEthernet1/0
description WAN
ip address 10.0.1.1 255.255.255.0
interface FastEthernet1/1
!
description LAN
ip address 192.168.1.1 255.255.255.0
!
interface Loopback0
ip address 1.1.1.1 255.255.255.255
!
ip route 0.0.0.0 0.0.0.0 10.0.1.99
!
R2
interface FastEthernet1/1
description lan
ip address 192.168.1.2 255.255.255.0
!
interface FastEthernet1/0
description wan
ip address 10.0.2.2 255.255.255.0
!
interface Loopback0
ip address 2.2.2.2 255.255.255.255
!
ip route 0.0.0.0 0.0.0.0 10.0.2.99
!
R10
!
interface Loopback0
ip address 10.10.10.10 255.255.255.255
!
!
interface FastEthernet1/0
description wan
ip address 10.0.10.10 255.255.255.0
!
interface FastEthernet1/1
description lan
ip address 192.168.2.10 255.255.255.0
delay 1000
!
R11
interface Loopback0
ip address 11.11.11.11 255.255.255.255
!
interface FastEthernet1/0
description wan
ip address 10.0.11.11 255.255.255.0
!
interface FastEthernet1/1
description lan
ip address 192.168.2.11 255.255.255.0
delay 1050
!
ip route 0.0.0.0 0.0.0.0 10.0.11.99
!
R20
!
interface Loopback0
ip address 20.20.20.20 255.255.255.255
!
interface FastEthernet1/0
description wan
ip address 10.0.20.20 255.255.255.0
!
interface FastEthernet1/1
description lan
ip address 192.168.3.20 255.255.255.0
!
ip route 0.0.0.0 0.0.0.0 10.0.20.99
!
Let start with HSRP on Hubs:
R1
interface FastEthernet1/1
description LAN
ip address 192.168.1.1 255.255.255.0
delay 1000
duplex full
speed auto
!virtual ip
standby 1 ip 192.168.1.254
!Virtual set priority for this router higher than R2
standby 1 priority 20
!If R1 has a highier priority become the active router
standby 1 preempt
standby 1 name HAGroup
!If Fa1/0 fails R1 is useless and needs to become standby
standby 1 track FastEthernet1/0
!
R2
interface FastEthernet1/1
description lan
ip address 192.168.1.2 255.255.255.0
delay 1050
duplex auto
speed auto
standby 1 ip 192.168.1.254
standby 1 priority 19
standby 1 preempt
standby 1 name HAGroup
standby 1 track FastEthernet1/0
!
The above setup is almost identical at Site2 (the other site with HSRP)
Now on to the Tunnels and the DMVPN networks itself. Here is the basic layout of the network:
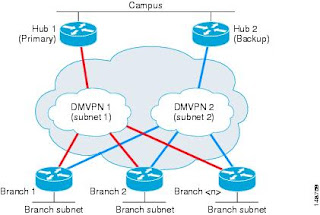
As you can see, we are infact running two DMVPN networks, and each spoke as an interface to each network.
Lets do the Hubs first:
R1
interface Tunnel0
!IP of tunnel interface
ip address 172.12.123.1 255.255.255.0
!Stop IP from taking "shortcuts"
no ip redirects
ip mtu 1400
ip nhrp map multicast dynamic
!Unique to the network, same number on each hub,spoke
ip nhrp network-id 1
ip nhrp holdtime 450
ip tcp adjust-mss 1360
!Needed for EIGRP
no ip split-horizon eigrp 100
!Tweak EIGRP metrics to prefer this router
delay 1000
!Tunnels out interface
tunnel source FastEthernet1/0
!Set tunnel mode
tunnel mode gre multipoint
!Each tunnel has its own "password"
tunnel key 100000
!Add IPSec
tunnel protection ipsec profile TUN-PROFILE
Notice that R1 is the Hub spoke for 172.12.123.0/24 network
R2
!
interface Tunnel0
ip address 172.12.124.2 255.255.255.0
no ip redirects
ip mtu 1400
ip nhrp map multicast dynamic
ip nhrp network-id 2
ip nhrp holdtime 450
ip tcp adjust-mss 1360
no ip split-horizon eigrp 100
!tweak EIGRP metric so that R1 is preferred
delay 1050
tunnel source FastEthernet1/0
tunnel mode gre multipoint
!Password
tunnel key 100001
tunnel protection ipsec profile TUN-PROFILE
!
Now R20
First tunnel to join network 1
interface Tunnel0
ip address 172.12.123.20 255.255.255.0
ip mtu 1400
ip nhrp map 172.12.123.1 10.0.1.1
ip nhrp network-id 1
ip nhrp holdtime 450
ip nhrp nhs 172.12.123.1
ip tcp adjust-mss 1360
tunnel source FastEthernet1/0
tunnel destination 10.0.1.1
tunnel key 100000
tunnel protection ipsec profile TUN-PROFILE
!
Second Tunnel to join network 2
!
interface Tunnel1
ip address 172.12.124.20 255.255.255.0
ip mtu 1400
ip nhrp map 172.12.124.2 10.0.2.2
ip nhrp network-id 2
ip nhrp holdtime 450
ip nhrp nhs 172.12.124.2
ip tcp adjust-mss 1360
tunnel source FastEthernet1/0
tunnel destination 10.0.2.2
tunnel key 100001
tunnel protection ipsec profile TUN-PROFILE
!
Now R10
!network 1 -->
interface Tunnel0
ip address 172.12.123.10 255.255.255.0
ip mtu 1400
ip nhrp map 172.12.123.1 10.0.1.1
ip nhrp network-id 1
ip nhrp holdtime 450
ip nhrp nhs 172.12.123.1
ip tcp adjust-mss 1360
delay 1000
tunnel source FastEthernet1/0
tunnel destination 10.0.1.1
tunnel key 100000
tunnel protection ipsec profile TUN-PROFILE
!
!
!Network 2 ----->
interface Tunnel1
ip address 172.12.124.10 255.255.255.0
ip mtu 1400
ip nhrp map 172.12.124.2 10.0.2.2
ip nhrp network-id 2
ip nhrp holdtime 450
ip nhrp nhs 172.12.124.2
ip tcp adjust-mss 1360
tunnel source FastEthernet1/0
tunnel destination 10.0.2.2
tunnel key 100001
tunnel protection ipsec profile TUN-PROFILE
!
R11
!Network 1 --->
interface Tunnel0
ip address 172.12.123.11 255.255.255.0
ip mtu 1400
ip nhrp map 172.12.123.1 10.0.1.1
ip nhrp network-id 1
ip nhrp holdtime 450
ip nhrp nhs 172.12.123.1
ip tcp adjust-mss 1360
delay 1050
tunnel source FastEthernet1/0
tunnel destination 10.0.1.1
tunnel key 100000
tunnel protection ipsec profile TUN-PROFILE
!Network 2--->
interface Tunnel1
ip address 172.12.124.11 255.255.255.0
ip mtu 1400
ip nhrp map 172.12.124.2 10.0.2.2
ip nhrp network-id 2
ip nhrp holdtime 450
ip nhrp nhs 172.12.124.2
ip tcp adjust-mss 1360
tunnel source FastEthernet1/0
tunnel destination 10.0.2.2
tunnel key 100001
tunnel protection ipsec profile TUN-PROFILE
!
Now EIGRP network configuration, notice how we do not bring in the WAN network:
R1
router eigrp 100
network 1.1.1.1 0.0.0.0
network 172.12.123.0 0.0.0.255
network 192.168.1.0
no auto-summary
!
R2
router eigrp 100
network 2.2.2.2 0.0.0.0
network 172.12.124.0 0.0.0.255
network 192.168.1.0
no auto-summary
!
R20
router eigrp 100
network 20.20.20.20 0.0.0.0
network 172.12.123.0 0.0.0.255
network 172.12.124.0 0.0.0.255
network 192.168.3.0
no auto-summary
!
R10
!
router eigrp 100
network 10.10.10.10 0.0.0.0
network 172.12.123.0 0.0.0.255
network 172.12.124.0 0.0.0.255
network 192.168.2.0
no auto-summary
!
R11
!
router eigrp 100
network 11.11.11.11 0.0.0.0
network 172.12.123.0 0.0.0.255
network 172.12.124.0 0.0.0.255
network 192.168.2.0
no auto-summary
!
IPSec Configuration is almost identical for each router so here is just one example:
!
crypto isakmp policy 100
encr aes
authentication pre-share
group 2
crypto isakmp key letmein address 0.0.0.0 0.0.0.0
crypto isakmp keepalive 10
!
!
crypto ipsec transform-set TUN-TRANSFORM esp-aes esp-sha-hmac
!
crypto ipsec profile TUN-PROFILE
set transform-set TUN-TRANSFORM
!
And that should be it!
Here is a video of me with the lab,trying to break it!
DMVPN - High Availability - Testing Failure from Richard Vimeo on Vimeo.
Enjoy!