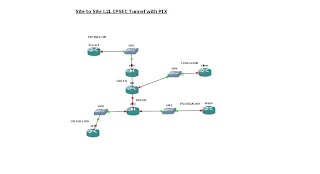
So lets start from the Remote Office "FW2"
First we need to set up ASA:
FW2
!
interface Ethernet0
nameif Outside
security-level 0
ip address 10.0.2.2 255.255.255.0
!
interface Ethernet1
nameif DMZ
security-level 50
ip address 192.168.20.2 255.255.255.0
!
interface Ethernet2
nameif Inside
security-level 100
ip address 192.168.2.2 255.255.255.0
!
Now NAT:
nat (Inside) 1 0.0.0.0 0.0.0.0
!Most people might like global (Outside) 1 interface instead
global (Outside) 1 10.0.2.50
Notice the "1" above, that ties the entrys together essentially saying on "these people on the inside (0.0.0.0) (everyone) are translated to this address "10.0.2.50" on the outside.
Now for testing we want to allow ICMP to the firewall
access-list WAN_IN extended permit icmp any any
Then assign it to an interface:
access-group WAN_IN in interface Outside
Add a default route:
route Outside 0.0.0.0 0.0.0.0 10.0.2.10 1
Ok we now have "internet access"
Next we need to setup the web server(192.168.20.100) with 1-to-1 nat:
nat (DMZ) 2 0.0.0.0 0.0.0.0
global (Outside) 2 10.0.2.100
static (DMZ,Outside) 10.0.2.100 192.168.20.100 netmask 255.255.255.255
Now NAT is setup, we actually need to let something through:
access-list WAN_IN extended permit tcp any host 10.0.2.100 eq telnet
access-list WAN_IN extended permit tcp any host 10.0.2.100 eq http
ok that was easy :)
Now for the HQ site:
First setup the pix:
FW1
interface Ethernet0
nameif outside
security-level 0
ip address 10.0.1.1 255.255.255.0
!
interface Ethernet1
nameif inside
security-level 100
ip address 192.168.1.1 255.255.255.0
!
Now NAT for FW1:
nat (inside) 1 0.0.0.0 0.0.0.0
global (outside) 1 interface
Ok now the tough part, actually this should be the easy part as we have done IPSec to death so far on the blog, and although the syntax looks different, actually typing it is pretty much the same as IOS.
One FW2
Set up an ISAKMP Policy:
crypto isakmp policy 100
authentication pre-share
encryption aes
hash sha
group 2
lifetime 86400
Then a Transform Set:
crypto ipsec transform-set FW1-TRANSFORM esp-aes esp-sha-hmac
Specify the traffic we dont want NAT applied too:
access-list NO-NAT extended permit ip 192.168.1.0 255.255.255.0 192.168.2.0 255.255.255.0
nat (inside) 0 access-list NO-NAT
The 0 indicates "dont NAT this"
Bring it all together with a crypto map:
access-list IPSEC-TUN extended permit ip 192.168.1.0 255.255.255.0 192.168.2.0 255.255.255.0
crypto map FW1 10 match address IPSEC-TUN
crypto map FW1 10 set peer 10.0.2.2
crypto map FW1 10 set transform-set FW1-TRANSFORM
Enable it on an interface:
crypto map FW1 interface outside
Add a tunnel group (if it is not already done for you)
tunnel-group 10.0.2.2 type ipsec-l2l
tunnel-group 10.0.2.2 ipsec-attributes
pre-shared-key letmein
Actually allow ISAKMP to connect to the outside interface:
crypto isakmp enable outside
Then the reverse/same on FW1:
access-list IPSEC-TUN extended permit ip 192.168.1.0 255.255.255.0 192.168.2.0 255.255.255.0
access-list NO-NAT extended permit ip 192.168.1.0 255.255.255.0 192.168.2.0 255.255.255.0
nat (inside) 0 access-list NO-NAT
crypto ipsec transform-set FW1-TRANSFORM esp-aes esp-sha-hmac
crypto map FW1 10 match address IPSEC-TUN
crypto map FW1 10 set peer 10.0.2.2
crypto map FW1 10 set transform-set FW1-TRANSFORM
crypto map FW1 interface outside
crypto isakmp enable outside
crypto isakmp policy 100
authentication pre-share
encryption aes
hash sha
group 2
lifetime 86400
tunnel-group 10.0.2.2 type ipsec-l2l
tunnel-group 10.0.2.2 ipsec-attributes
pre-shared-key *
prompt hostname context
Done!
Pix/ASA does alot for you in l2l ipsec vpns..and they still dont call it "easy vpn" :)